OSINT
Uncovering the Power of OSINT
As a security analyst, one of the most critical tasks is gathering information to assess vulnerabilities, detect threats, and mitigate risks. Open Source Intelligence (OSINT) is an essential methodology in the cybersecurity landscape, utilizing publicly available data to uncover insights that can be used in threat analysis, investigations, and incident response. In this blog post, I will explore the significance of OSINT in cybersecurity and delve into one powerful resource that assists analysts in conducting OSINT investigations—OSINT Framework.
What is OSINT?
Open Source Intelligence (OSINT) involves collecting and analyzing data from open, publicly accessible sources. This can include anything from social media posts, public databases, and forums to government publications and website metadata. While OSINT is often associated with cybersecurity, it is used in a variety of fields, including law enforcement, journalism, and corporate investigations.
The power of OSINT lies in its ability to gather actionable intelligence without requiring specialized access or intrusive methods. Security analysts can use OSINT to identify potential vulnerabilities, profile threat actors, and stay ahead of emerging cyber threats.
OSINT Framework: An All-in-One Resource for Security Analysts
The OSINT Framework is an extensive and well-organized web-based collection of OSINT tools and resources. The primary purpose of this framework is to help security professionals, researchers, and enthusiasts navigate the ever-growing landscape of OSINT tools. The platform provides links to a variety of tools and resources across different categories, making it a go-to resource for conducting thorough intelligence-gathering efforts.
The framework itself is built on a visual tree structure, as shown in the image below. Each category of tools branches out into subcategories, leading to specific tools for conducting research, analysis, and discovery.
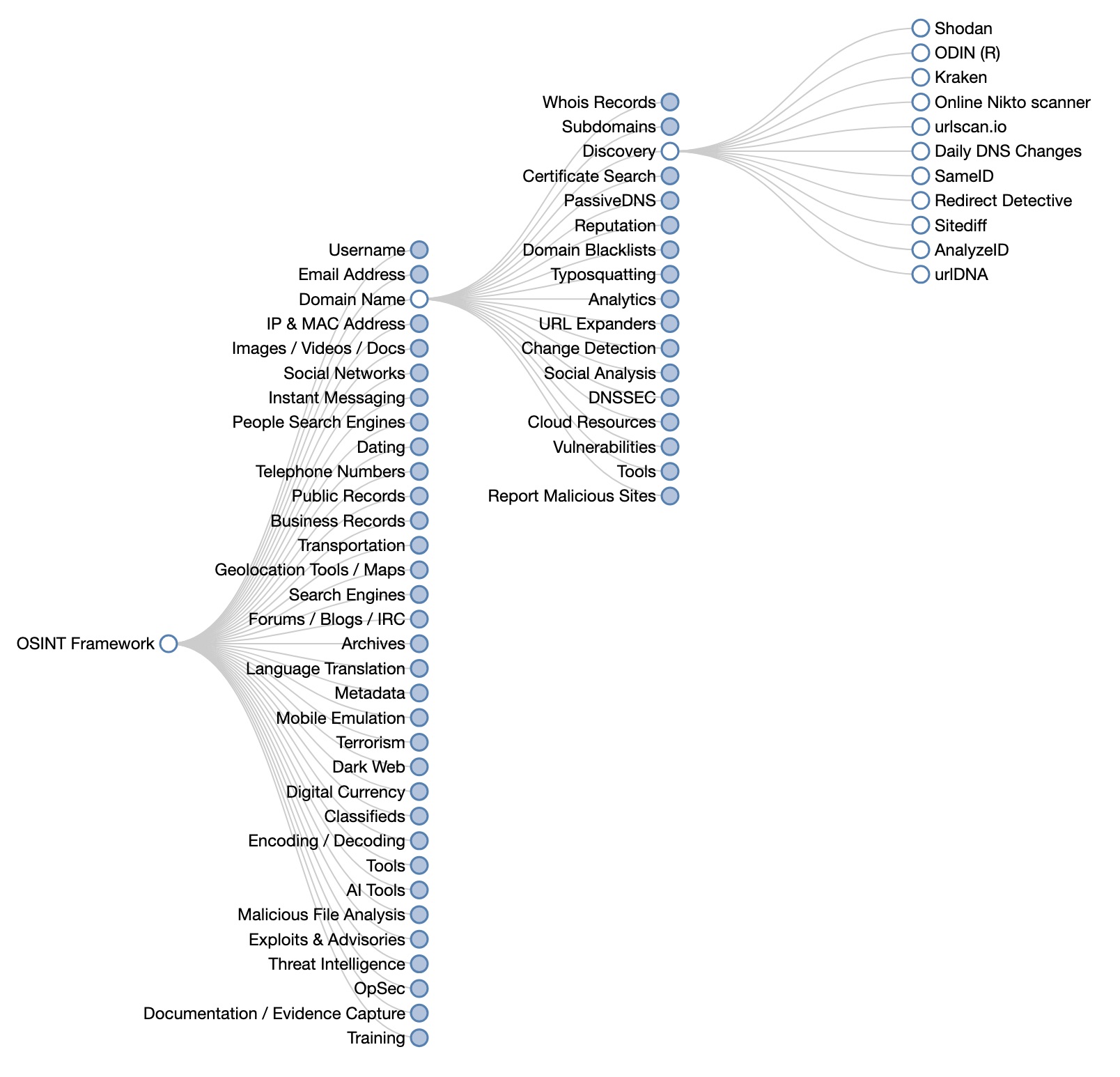

Let’s dive deeper into some of the critical sections of the OSINT Framework and their relevance to cybersecurity and security analysis.
Key Categories of OSINT Framework for Security Analysts
1. Domain and IP Address Discovery
OSINT Framework offers tools to analyze domain names and IP addresses, which are crucial for identifying malicious infrastructure or uncovering phishing attempts. This section includes tools for:
- Whois Records: Fetches registration data for domains to track ownership history.
- Subdomains: Helps in identifying related subdomains of a target, which may reveal vulnerable services.
- Passive DNS: A method to track historical DNS resolutions, useful for mapping an organization’s digital footprint.
Example tools: Shodan, ODIN (R), and Daily DNS Changes.
2. Social Network Analysis
Social media can be a treasure trove of information, whether it’s investigating cybercriminals or monitoring organizational vulnerabilities. The OSINT Framework offers various tools to search usernames, check social networks, and analyze patterns of behavior. This section provides access to resources like People Search Engines and tools for investigating activity across platforms like Facebook, Instagram, and Twitter.
3. Email Address and Telephone Number Lookups
Being able to trace email addresses and phone numbers is invaluable for phishing investigations or tracking suspicious communication. This section includes resources for verifying whether contact details are tied to fraudulent activity. Analysts can use services like Email Address Search Engines or telephone number lookup services to link suspicious data points to real-world entities.
4. Metadata and File Analysis
Often, analyzing the metadata of files (e.g., documents, images) can reveal hidden information, such as the origin of a file, the software used to create it, or its modification history. This can provide crucial intelligence in investigations. The OSINT Framework includes tools for pulling metadata from a wide range of file formats, such as PDFs and images, allowing security analysts to dig deeper into potentially malicious files.
5. Malicious File and Vulnerability Analysis
Understanding the behavior of malicious files, such as malware, is essential for incident response and vulnerability management. This section of the framework offers tools for scanning files and identifying known vulnerabilities. Popular tools included in this category are VirusTotal and exploit databases like ExploitDB.
6. Geolocation and Maps
Tracking the physical location of an IP address or examining geographic patterns of attacks can provide significant insights. OSINT Framework includes geolocation tools that can help pinpoint the source of attacks or track the movement of devices. Tools like GeoIP lookup and mapping utilities are provided to assist analysts in tracing malicious actors geographically.
How to Use OSINT Framework Effectively
Security analysts can use OSINT Framework to streamline investigations and intelligence gathering. To maximize its potential:
- Start with a clear objective: Whether you’re trying to identify threat actors, profile an organization’s attack surface, or analyze malicious emails, define your goal before diving into tools.
- Leverage multiple tools: The OSINT Framework provides a wealth of options; combining data from various sources increases the accuracy and depth of your findings.
- Stay ethical: Always ensure that your OSINT activities are legal and ethical. Avoid crossing boundaries that may infringe on privacy or violate local laws.
Conclusion
In the world of cybersecurity, knowledge is power. OSINT is one of the most accessible and potent ways to gather that knowledge without requiring privileged access. With platforms like OSINT Framework, security analysts have a comprehensive resource at their disposal to uncover threats, analyze vulnerabilities, and ultimately protect the digital assets they are responsible for.
If you’re interested in learning more about OSINT or exploring the tools provided by OSINT Framework, visit their site and dive into the wide range of resources available. Whether you’re investigating a potential threat or conducting a routine security audit, OSINT Framework can be a valuable asset in your cybersecurity toolkit.
Feel free to share your thoughts and experiences using OSINT in the comments below. Have you discovered any interesting findings or tools worth mentioning? Let’s discuss!
Enjoy Reading This Article?
Here are some more articles you might like to read next: