Virtual Private Network
Virtual Private Networks (VPNs): The Cornerstone of Secure Communication
In today’s hyper-connected world, privacy and security are becoming more critical than ever. With a rise in cyberattacks and an increasing amount of sensitive data being transmitted across the internet, it’s crucial to understand how to protect yourself. One of the most effective tools for ensuring secure and private online communication is the Virtual Private Network (VPN).
For anyone working in IT security or studying for certifications like Security+, mastering the concept and use of VPNs is essential. In this post, I’ll break down what a VPN is, how it works, its benefits, and why it’s indispensable for cybersecurity.
What is a VPN?
A VPN, or Virtual Private Network, is a service that allows you to create a secure connection to another network over the internet. By using a VPN, all your internet traffic is encrypted and routed through a remote server, masking your IP address and shielding your activities from prying eyes, such as hackers, ISPs, and even governments. Think of a VPN as a protective tunnel between your device and the internet, where everything that travels through it is secured by encryption.
While VPNs are widely known as tools for increasing privacy, their use extends far beyond hiding your location. They are vital for secure communications, especially in corporate environments where employees may need to access internal systems remotely.
virtual private networks (vpns): the cornerstone of Secure Communication
In today’s hyper-connected world, privacy and security are becoming more critical than ever. With a rise in cyberattacks and an increasing amount of sensitive data being transmitted across the internet, it’s crucial to understand how to protect yourself. One of the most effective tools for ensuring secure and private online communication is the Virtual Private Network (VPN).
For anyone working in IT security or studying for certifications like Security+, mastering the concept and use of VPNs is essential. In this post, I’ll break down what a VPN is, how it works, its benefits, and why it’s indispensable for cybersecurity.
What is a VPN?
A VPN, or Virtual Private Network, is a service that allows you to create a secure connection to another network over the internet. By using a VPN, all your internet traffic is encrypted and routed through a remote server, masking your IP address and shielding your activities from prying eyes, such as hackers, ISPs, and even governments. Think of a VPN as a protective tunnel between your device and the internet, where everything that travels through it is secured by encryption.
While VPNs are widely known as tools for increasing privacy, their use extends far beyond hiding your location. They are vital for secure communications, especially in corporate environments where employees may need to access internal systems remotely.
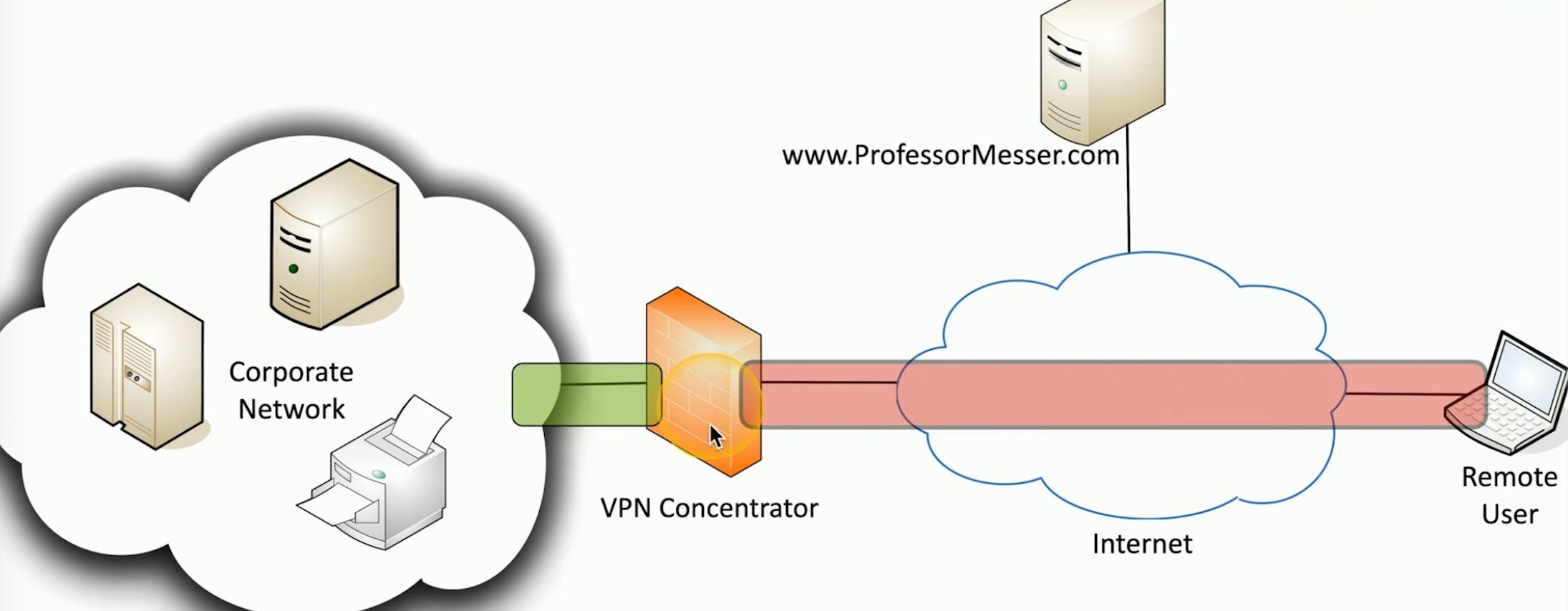
How Does a VPN Work?
When you use a VPN, your device establishes an encrypted connection with a VPN server. Instead of directly accessing the internet, all your traffic is first routed through the VPN server. This has several implications for security and privacy:
- Encryption: Your data is encrypted before it leaves your device. This encryption ensures that even if someone intercepts your data in transit, they cannot read it.
- IP Masking: The VPN server replaces your real IP address with its own. As a result, websites and services only see the VPN server’s IP, providing a layer of anonymity.
- Routing: Your internet traffic is routed through the VPN server, which can be located anywhere in the world. This allows you to appear as though you’re accessing the internet from a different location, which is useful for bypassing geo-restrictions.
VPNs in Action: Real-World Use Cases
While VPNs provide security and privacy for individual users, their real value shines in enterprise environments where data protection is a top priority. As organizations increasingly adopt remote work and cloud-based services, VPNs become vital for maintaining secure communication across different platforms and locations.
1. Site-to-Site VPNs: Connecting Networks
A Site-to-Site VPN is often used by companies with multiple branch offices or remote data centers. This type of VPN creates a secure tunnel between two or more different networks, allowing them to communicate as if they were in the same physical location. This is particularly useful for companies that need to transfer large amounts of data securely between locations, such as between headquarters and a satellite office.
In this setup, VPN concentrators (specialized devices for managing VPN connections) play a crucial role by establishing and maintaining the VPN tunnel. This ensures that both sites can access shared resources, like internal servers, with the same level of security as they would on a local network.
Example for Security+ Context: Understanding how VPN concentrators work is essential for the Security+ exam. A VPN concentrator is a device that handles large-scale VPN operations, encrypting and decrypting data for multiple users or devices at once. In exam questions, these concentrators might be referenced in scenarios that involve remote workers or securing communications between branches of a business.
2. Remote Access VPN: Secure Telecommuting
In today’s world, remote work is becoming the norm for many companies, and securing access to internal systems is paramount. A Remote Access VPN allows employees working from home or traveling to securely connect to their company’s internal network. This is particularly useful for accessing files, internal databases, or even specific applications like email servers or collaboration platforms.
In this scenario, an employee’s device establishes a secure connection to the company’s VPN server, and once the connection is authenticated, they can work as though they were physically on the company’s premises. Remote access VPNs often utilize multi-factor authentication (MFA) to ensure that only authorized users can connect.
Example for Security+ Context: The CIA Triad (Confidentiality, Integrity, and Availability) is a key concept in Security+. VPNs ensure Confidentiality by encrypting data sent over the internet, Integrity by ensuring that data is not altered in transit, and Availability by allowing employees to access resources remotely and securely. You may encounter exam questions that challenge you to choose VPN solutions that meet specific goals, such as maintaining confidentiality.
3. VPNs and Cloud Security
As businesses migrate more infrastructure and applications to the cloud, securing these cloud-based resources becomes a priority. VPNs can be used in conjunction with cloud services to secure connections between on-premises networks and cloud environments, ensuring that data being transferred to or from the cloud is encrypted and protected from unauthorized access.
Many cloud service providers, such as Amazon Web Services (AWS) and Microsoft Azure, offer their own VPN services that allow organizations to create private connections between their internal networks and cloud-based infrastructure. This approach, often called a Hybrid Cloud VPN, bridges the gap between on-premise data centers and cloud environments.
Example for Security+ Context: In the Security+ exam, you may encounter scenarios involving cloud security. VPNs are a practical solution for securing connections between local and cloud environments, ensuring that sensitive data stored in the cloud is transmitted securely. You should be familiar with the concept of Hybrid Cloud and how VPNs play a role in securing cloud interactions.
Relevant Security+ Concepts Tied to VPNs
Several key terms and concepts from Security+ are tied to the functionality and importance of VPNs. Let’s explore a few:
1. Tunneling
Tunneling is a crucial concept when it comes to VPNs. It involves encapsulating one type of network traffic inside another, effectively creating a “tunnel” through which data can securely pass. VPNs use tunneling protocols like L2TP/IPsec and OpenVPN to create secure channels for data transmission. This encapsulation allows private data to travel across public networks without being exposed.
For the Security+ exam, it’s important to understand how different tunneling protocols work and when each one should be used. For instance, IPsec is commonly used for securing traffic at the IP layer, while SSL/TLS provides security at the transport layer.
2. Encryption Protocols
Encryption is the backbone of any VPN. VPNs use different encryption protocols to secure the data being transmitted over the network. You’ll need to understand the basics of these protocols for Security+, especially their strengths and weaknesses. Key encryption protocols include:
- AES (Advanced Encryption Standard): A widely used encryption method that offers strong security and is often used in VPNs.
- DES/3DES (Data Encryption Standard/Triple DES): While less secure than AES, these older encryption methods are still sometimes used, particularly in legacy systems.
- SSL/TLS (Secure Sockets Layer/Transport Layer Security): These are the primary encryption protocols used by OpenVPN for securing data traffic.
In the exam, understanding the use of these encryption methods and how they apply to VPNs is critical.
3. Authentication Methods
VPNs often incorporate multiple authentication methods to ensure that only authorized users can access the network. This can include:
- Pre-shared Keys (PSK): A shared secret key that is used to authenticate the user and the VPN server.
- Digital Certificates: These provide more secure authentication by verifying the identity of the user through a trusted certificate authority.
- Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring users to provide more than one form of verification (e.g., a password and a one-time code from a mobile app).
For Security+, understanding these authentication mechanisms is key, especially when securing remote access through VPNs.
Conclusion: VPNs in the Security+ Journey
As I study for Security+, VPNs have been a key topic in understanding how to secure data, especially in today’s increasingly decentralized and mobile workforce. Whether it’s protecting sensitive data in transit, maintaining secure remote access, or simply safeguarding personal privacy, VPNs are an essential part of any security strategy.
For those of us entering the world of IT security, mastering VPNs is just the beginning. They offer a tangible example of how encryption, tunneling, and security protocols come together to protect data in real-world scenarios.
How Does a VPN Work?
When you use a VPN, your device establishes an encrypted connection with a VPN server. Instead of directly accessing the internet, all your traffic is first routed through the VPN server. This has several implications for security and privacy:
- Encryption: Your data is encrypted before it leaves your device. This encryption ensures that even if someone intercepts your data in transit, they cannot read it.
- IP Masking: The VPN server replaces your real IP address with its own. As a result, websites and services only see the VPN server’s IP, providing a layer of anonymity.
- Routing: Your internet traffic is routed through the VPN server, which can be located anywhere in the world. This allows you to appear as though you’re accessing the internet from a different location, which is useful for bypassing geo-restrictions.
VPNs in Action: Real-World Use Cases
While VPNs provide security and privacy for individual users, their real value shines in enterprise environments where data protection is a top priority. As organizations increasingly adopt remote work and cloud-based services, VPNs become vital for maintaining secure communication across different platforms and locations.
1. Site-to-Site VPNs: Connecting Networks
A Site-to-Site VPN is often used by companies with multiple branch offices or remote data centers. This type of VPN creates a secure tunnel between two or more different networks, allowing them to communicate as if they were in the same physical location. This is particularly useful for companies that need to transfer large amounts of data securely between locations, such as between headquarters and a satellite office.
In this setup, VPN concentrators (specialized devices for managing VPN connections) play a crucial role by establishing and maintaining the VPN tunnel. This ensures that both sites can access shared resources, like internal servers, with the same level of security as they would on a local network.
Example for Security+ Context: Understanding how VPN concentrators work is essential for the Security+ exam. A VPN concentrator is a device that handles large-scale VPN operations, encrypting and decrypting data for multiple users or devices at once. In exam questions, these concentrators might be referenced in scenarios that involve remote workers or securing communications between branches of a business.
2. Remote Access VPN: Secure Telecommuting
In today’s world, remote work is becoming the norm for many companies, and securing access to internal systems is paramount. A Remote Access VPN allows employees working from home or traveling to securely connect to their company’s internal network. This is particularly useful for accessing files, internal databases, or even specific applications like email servers or collaboration platforms.
In this scenario, an employee’s device establishes a secure connection to the company’s VPN server, and once the connection is authenticated, they can work as though they were physically on the company’s premises. Remote access VPNs often utilize multi-factor authentication (MFA) to ensure that only authorized users can connect.
Example for Security+ Context: The CIA Triad (Confidentiality, Integrity, and Availability) is a key concept in Security+. VPNs ensure Confidentiality by encrypting data sent over the internet, Integrity by ensuring that data is not altered in transit, and Availability by allowing employees to access resources remotely and securely. You may encounter exam questions that challenge you to choose VPN solutions that meet specific goals, such as maintaining confidentiality.
3. VPNs and Cloud Security
As businesses migrate more infrastructure and applications to the cloud, securing these cloud-based resources becomes a priority. VPNs can be used in conjunction with cloud services to secure connections between on-premises networks and cloud environments, ensuring that data being transferred to or from the cloud is encrypted and protected from unauthorized access.
Many cloud service providers, such as Amazon Web Services (AWS) and Microsoft Azure, offer their own VPN services that allow organizations to create private connections between their internal networks and cloud-based infrastructure. This approach, often called a Hybrid Cloud VPN, bridges the gap between on-premise data centers and cloud environments.
Example for Security+ Context: In the Security+ exam, you may encounter scenarios involving cloud security. VPNs are a practical solution for securing connections between local and cloud environments, ensuring that sensitive data stored in the cloud is transmitted securely. You should be familiar with the concept of Hybrid Cloud and how VPNs play a role in securing cloud interactions.
Relevant Security+ Concepts Tied to VPNs
Several key terms and concepts from Security+ are tied to the functionality and importance of VPNs. Let’s explore a few:
1. Tunneling
Tunneling is a crucial concept when it comes to VPNs. It involves encapsulating one type of network traffic inside another, effectively creating a “tunnel” through which data can securely pass. VPNs use tunneling protocols like L2TP/IPsec and OpenVPN to create secure channels for data transmission. This encapsulation allows private data to travel across public networks without being exposed.
For the Security+ exam, it’s important to understand how different tunneling protocols work and when each one should be used. For instance, IPsec is commonly used for securing traffic at the IP layer, while SSL/TLS provides security at the transport layer.
2. Encryption Protocols
Encryption is the backbone of any VPN. VPNs use different encryption protocols to secure the data being transmitted over the network. You’ll need to understand the basics of these protocols for Security+, especially their strengths and weaknesses. Key encryption protocols include:
- AES (Advanced Encryption Standard): A widely used encryption method that offers strong security and is often used in VPNs.
- DES/3DES (Data Encryption Standard/Triple DES): While less secure than AES, these older encryption methods are still sometimes used, particularly in legacy systems.
- SSL/TLS (Secure Sockets Layer/Transport Layer Security): These are the primary encryption protocols used by OpenVPN for securing data traffic.
In the exam, understanding the use of these encryption methods and how they apply to VPNs is critical.
3. Authentication Methods
VPNs often incorporate multiple authentication methods to ensure that only authorized users can access the network. This can include:
- Pre-shared Keys (PSK): A shared secret key that is used to authenticate the user and the VPN server.
- Digital Certificates: These provide more secure authentication by verifying the identity of the user through a trusted certificate authority.
- Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring users to provide more than one form of verification (e.g., a password and a one-time code from a mobile app).
For Security+, understanding these authentication mechanisms is key, especially when securing remote access through VPNs.
Conclusion: VPNs in the Security+ Journey
As I study for Security+, VPNs have been a key topic in understanding how to secure data, especially in today’s increasingly decentralized and mobile workforce. Whether it’s protecting sensitive data in transit, maintaining secure remote access, or simply safeguarding personal privacy, VPNs are an essential part of any security strategy.
For those of us entering the world of IT security, mastering VPNs is just the beginning. They offer a tangible example of how encryption, tunneling, and security protocols come together to protect data in real-world scenarios.
Enjoy Reading This Article?
Here are some more articles you might like to read next: